The importance of using Cloud Technologies to connect to the Cloud
From the beginning of the packet networking era, all vendors recommended to use the same solution end to end. The use of the same technology on both ends has multiple benefits and can guarantee 100% compatibility.
The same happens today when you want to connect to cloud services. The best performance is only achievable when using the same technology on both ends.
The family of Cloud Security Connectors (CSC) for Zscaler were created based on this principle: full compatibility between the branch and the cloud.
The following example shows a Zscaler customer that decided to replace their current router (with GRE tunnels to Zscaler) with the CSC-GRE. This is a good example of what happens before and after the installation of the CSC.
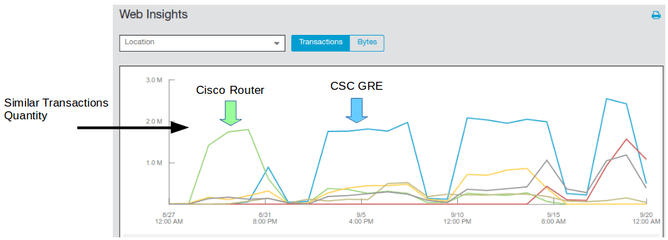
The following graph was taken from the Zscaler Console and shows the amount of Transactions (Http/s transactions: GET, POST, etc.) of the Location with the router first and the CSC-GRE after.
As you can see, the amount of transactions are similar. There is no a major difference. Users were using the web in the same way in both cases.
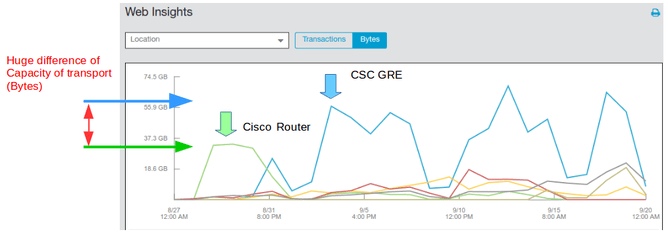
But, when you click “Bytes” per Location, the difference in performance is huge:
The Cloud Security Connector can move a significant more amount of Bytes than the router.
There are several reason for this: Firstly, the complexity required to be done on a Router in order to achieve high availability with Zscaler. You need to insert about 60 commands and more than 180 parameters (see: https://help.zscaler.com/zia/gre-configuration-example-cisco-881-isr) . This amount of parametrization has an impact on performance. Secondly, the edge routers are not the best in terms of CPU capacity. The CSC runs on Virtual Environment with Xeon processors and finally, the CSC has the perfect configuration for Zscaler with several tuning done at kernel level and on the TCP software.
But most important is that the benefits of this extra capacity was taken by Microsoft Cloud services. Analysing this extra amount of Bytes moved on the location we found that most of extra traffic was used by Office 365 and Windows Updates.
Zscaler has an excellent peering with Microsoft Cloud and if you want to get the most of it, you need to use the Cloud Security Connector.
Additionally you will receive the benefit of the simplicity of the CSC: No configuration is needed. Just fill a form with your IP addresses and download the software with the perfect configuration for Zscaler.
For more information, please, email as at: sales@maidenheadbridge.com or visit our page at: www.maidenheadbridge.com